We speak poetically of the Trust Graph, a web of light connecting human potential. But in the Lab, we speak in hashes, zero-knowledge proofs, and consensus mechanisms. The Trust Graph is not a metaphor, it is a cryptographically enforced, game-theoretically stable public ledger of promises made and kept. Its "soul" is not magic, but a brutal, elegant architecture designed to make lying more computationally expensive than telling the truth. Here, we deconstruct the engine.
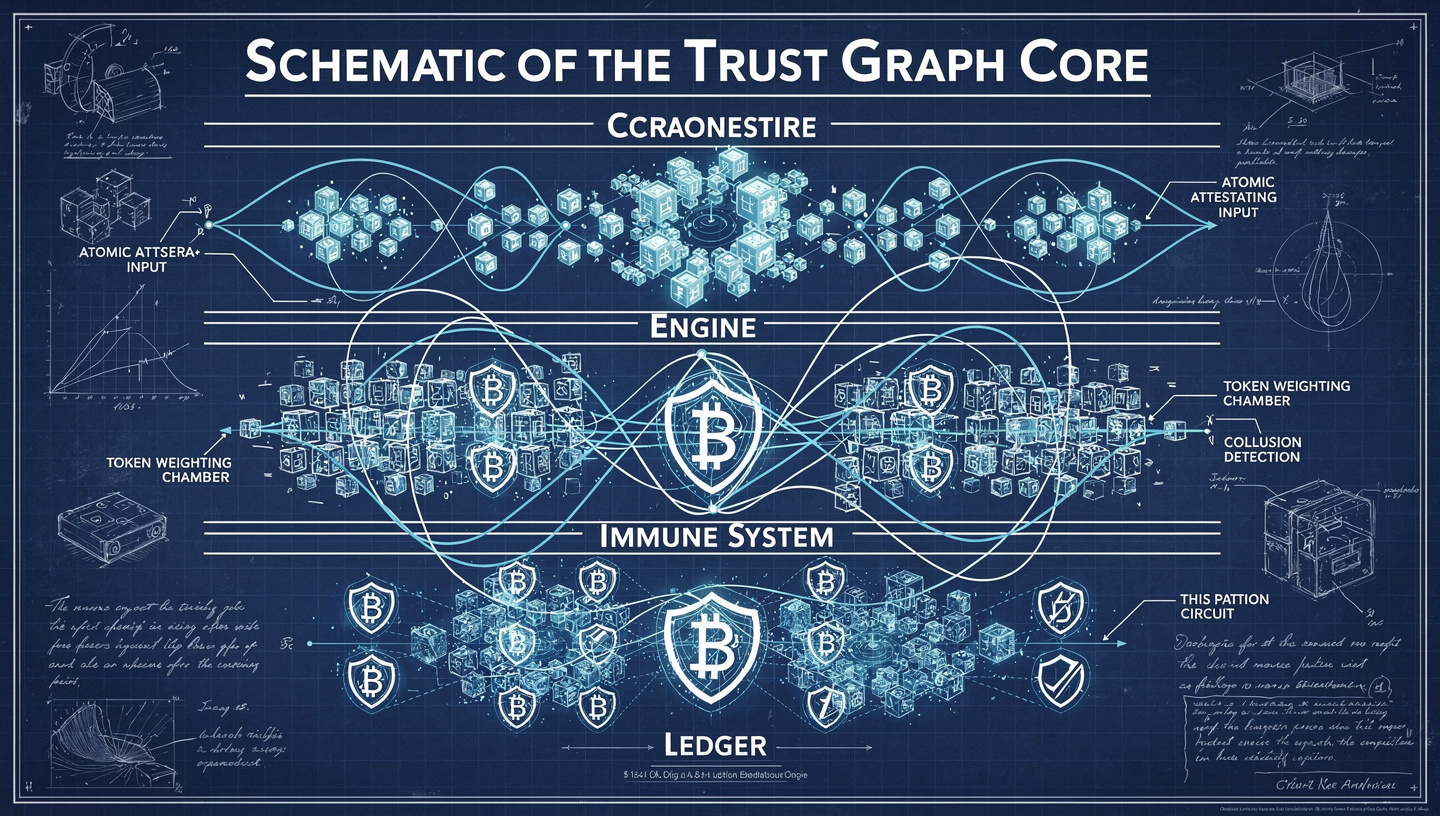
Layer 1: The Ledger of Atomic Truths
Every claim on a Unified Self "I delivered the code", "I resolved the dispute", "I mentored the junior developer" must be atomically verifiable. We use a modified blockchain tripe, not for currency, but for attestations. When Alice completes a project for Bob, they both sign a cryptographic hash of the outcome. This hash, along with similar ones from other collaborators, is anchored to a public, immutable ledger. The claim "Alice delivered" is now not an opinion, it is a consensus-verified fact. The graph is built from these trillions of atomic truths, not from subjective reviews.
Layer 2: The Reputation Engine & Tokenomics of Trust
Reputation isn't a score, it's a staked asset. When you earn a positive attestation, you don't get a point. You earn a non-transferable "Trust Token" specific to that skill context (TrustToken:Web3-Solidity-Development). These tokens have weight based on the reputational capital of the attester. A token from a node with a heavy, positive history in that domain weighs more. Your reputation in an area is the sum of the weighted tokens you hold. This creates a natural, anti-Sybil ecosystem: building fake reputation requires conspiring with high-trust nodes, who would jeopardize their own valuable capital by attesting falsely. Lying has a clear, immediate cost.
Layer 3: The Constraint Protocols â The First Law in Code
Our "First Law of Coordination" (a constraint for every protocol) is encoded here. For the power of the Trust Graph, the constraint is the Contextual Decay Function and the Right to Amend.
- Decay: A Trust Token for "React Development" from 2018 loses 10% of its weight per year unless reaffirmed by a new, verifiable project in that domain. This fights obsolescence.
- Right to Amend: A user can petition to "contextually seal" a past failure. A panel of peers and a Digital Shaman review the petition and subsequent history. If approved, a Seal of Context is attached to the old attestation, making it visible only in deep-due-diligence mode, not in general matching. This builds redemption into the data structure.
The Graph's Immune System: Anti-Collusion & Attack Vectors
The Lab's most vital work is stress-testing for failure modes.
- The "Praise Cartel" Attack: Several nodes inflate each other's reputations. Defense: Our algorithms detect circular attestation patterns and automatically de-weight tokens originating from closed clusters, pushing a discovery penalty that forces nodes to seek attestations from outside their cartel to grow.
- The "Blackmail" Attack: A malicious user threatens to give a false negative attestation. Defense: All negative attestations must include verifiable, platform-logged evidence of failure (e.g., missed milestones, broken code). Unsubstantiated negatives carry zero weight and penalize the attester's "Judgment Accuracy" score.
The Trust Graph's soul is a set of rules that make virtuous behavior the most strategically rational choice. We are not tracking reputation. We are architecting an economic game where the only winning move is to be reliably, verifiably trustworthy. The warmth of human connection is real, but it is secured by the cold, flawless logic of cryptography.





Be the first to leave a comment.